
If you haven’t heard, Google are driving through the reduction from 398-day to 90-day certificate lifecycles, as the new standard, whether the rest of us are ready for it or not! This is ultimately a good move for consumers though, as they’re seeking improve browser cyber security for internet users, through automated certificate management. Still, this move poses some significant implications for IT teams, so whether you manage just one or even ten thousand certificates, and are unsure what this means for you – we’ve got you covered.
Keep on reading to uncover more about the upcoming changes and how we can tackle this transformation together (and soon).
The important stuff:
Google recently announced their intentions to reduce the validity for public TLS (also known as SSL) certificates to 90 days, down from 398 days. This isn’t the first time this has been done, with the certificate lifestyle historically being 5,3,2, and now 1 year in length; soon to be 90 days. 90-day certificates are a 77.4% reduction in maximum term, from 398 days, and will be more than 4 times the workload within the year period.
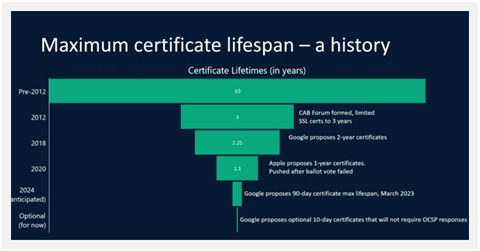
To be clear, this is not a Jisc led change, it is an industry wide decision. Google’s “Moving Forward, Together” roadmap, released on March 3rd, explains how it is their intention to introduce this change through the CA/B Forum Ballot Proposal yet Google are prepared to force this change through making sure every commercial public Certificate Authority (CA) follows suit, even if it is not accepted.
As a community, we cannot rule out the possibility of Google reducing certificate validity further. Google believe that shorter certificate lifecycles offer:
- Enhanced security by reducing the window of vulnerability
- Faster response to compromised certificates
- Facilitates the adoption of emerging security technologies and best practices
- Mitigates the risk of using outdated or compromised certificates
- Promotes regular certificate renewal and upkeep
The problem?
If you are reading this, it is probably because you deal with SSL certificates regularly. If you are not as familiar with certificate management and want to gain a wider understanding on the importance of web certificates, please check out our blog on – What are SSL certs and why do we need them?
It is crucial to understand the importance of SSL certificates, if we are to understand the effect that the 90-day change could and will have on the IT persona. By increasing the manual workload of IT teams from 1 to just over 4 times a year, this increases not only the margin for error, but the risk of security threats and operational challenges.
From past experiences, I think we can all agree that you are not safe leaving your certificate renewal to the last day, given their ability to take critical digital services offline. Consequently, if you want to prevent an outage, the 90-day change will mean that certificate life spans can now be considered as less than 90 days, in practicality.
With the rapid expansion of the web and consumer’s reliance on online trust and security in today’s digital environments, certificates remain an imperative. We are all aware of the risks if services are not correctly verified or protected. Although this change is coming rapidly, it’s in everyone’s interests to support this transformation, as the drive to automation seeks to future-proof our cyber security strategies, without increasing the management burden.
From Google’s side, they have stressed the significance of crypto agility i.e. the ability to respond to a change or threat in an agile and timely manner. Long lived crypto algorithms are becoming atypical moving forwards, thus, to achieve crypto agility, certificate agility is of the highest importance. We need to begin to foster environments where our cryptography can change rapidly, if needed.
Sectigo suggests automation protocols are the most effective method of replacing certificates moving forward, as they enable the following benefits for certificate replacement:
- Instant
- Error free
- Precision
- Ability to handle any volume
- Verifiable
Food for thought:
Here at Jisc, we are aware of the workload (and frustration) it takes to create and renew your certificates. Imagine what you do now multiplied by 4! If there ever was a time for automated certificate lifecycles, it is now. Automation is a critical part of the 90-day cert solution, reducing the manual workload that is soon to become impossible to keep up with by ensuring timely renewals, avoiding the disaster of certificate expiration and potential security risks.
Our provider, Sectigo, is built to automate the lifecycles of all digital certificates. As Sectigo has highlighted here, ACME is the preferred automated protocol for public certificate issuance and management.
The Automated Certificate Management Environment protocol (ACME) is a protocol for automating certificate lifecycle management communications between Certificate Authorities (CAs) and a company’s web servers, email systems, user devices, and any other place Public Key Infrastructure certificates (PKI) are used.
Sectigo suggests that IT teams rely on ACME more and more to help them address their scale and complexity challenges as it offers:
- an open standard with a full set of commands and robust error handling, making it easy to adopt both by the enterprise and CAs
- best of breed TLS and other PKI security practices for both IT teams tasked with implementing and managing valid PKI certificates and trusted CAs that adhere to strict authentication procedures
- ongoing enhancements and support by a community, not controlled by any one single vendor or organization
- flexibility to add and support backup CAs
- low cost, being free to use
Although ACME is one potential automation solution, there are many others out there. Jisc are currently working with GEANT to assess how we might offer support around CertBot, as an example.
We are currently surveying all our certificate service members to better establish their needs. We will be publishing more about your feedback on the need for solutions, support and guidance, and how we plan to address this, in the coming months.
Summary:
- What is changing: Certificate lifecycle from 398>90. Domain validation (DCV) to mirror this change
- When: November 2024 (estimated)
- What is staying the same: How to request a cert/ how to validate a domain
- Automation just went from a want to a need. Without automation you do not have certificate agility, you have a vulnerability
Recommended next steps:
- Find out what you own – rogue certs? Understand your portfolio so nothing goes unnoticed
- Assess automation solutions
- Implement automation
- Test automation ahead of the change
We hope that this blog post has been helpful. Please keep an eye out for updates from Jisc, Google and the CA/B Forum regarding the implementation timeline and enforcement dates and monitor industry best practices and recommendations for SSL/TLS certificates to stay updated with evolving security requirements.
For any feedback, queries, or questions please contact the service desk – certificates@jisc.ac.uk

One reply on “90-day Certificates Are Coming….”
A very good summary of an ultimately good change, if somewhat painful transition, to automation.